Cloud VM Platform Encryption
How can VM backups, snapshots, and live migration be secured?
Problem
VM backups, snapshots and live migration create files that encapsulate the entire VM. These files can then be copied or moved outside the application that the cloud consumer controls, making them vulnerable to attacks.
Solution
Encrypted containers are provided for use and storage of the various types of VM backups and replications.
Application
A key manager is used to manage keys for encryption of the various types of VM storage that are pre-provisioned to receive backups and snapshots of consumer VMs or to receive replications and live migrations.
Mechanisms
Cryptographic Key Management System, Virtual Server
Compound Patterns
Burst In, Burst Out to Private Cloud, Burst Out to Public Cloud, Cloud Authentication, Cloud Balancing, Elastic Environment, Infrastructure-as-a-Service (IaaS), Isolated Trust Boundary, Multitenant Environment, Platform-as-a-Service (PaaS), Private Cloud, Public Cloud, Resilient Environment, Resource Workload Management, Secure Burst Out to Private Cloud/Public Cloud, Software-as-a-Service (SaaS)
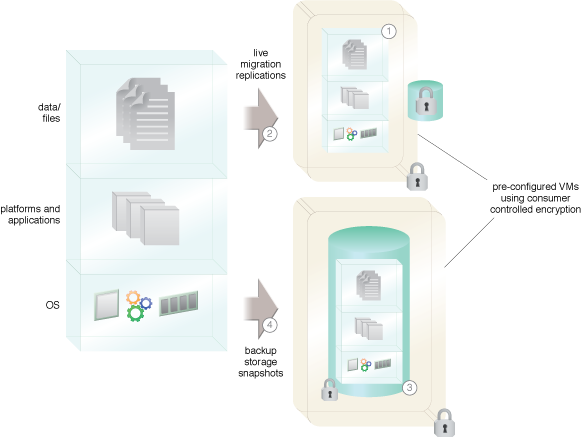
Pre-configured VMs encrypted with consumer controlled encryption.
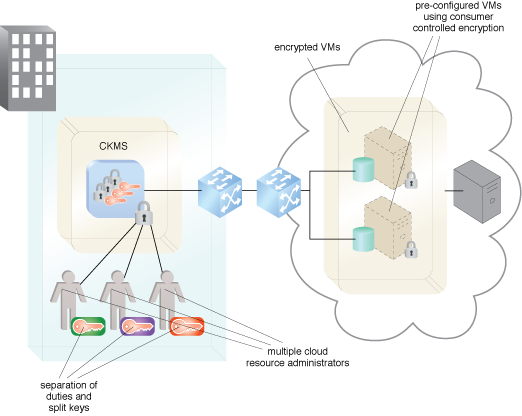
Key management and the Cloud VM Platform Encryption pattern.